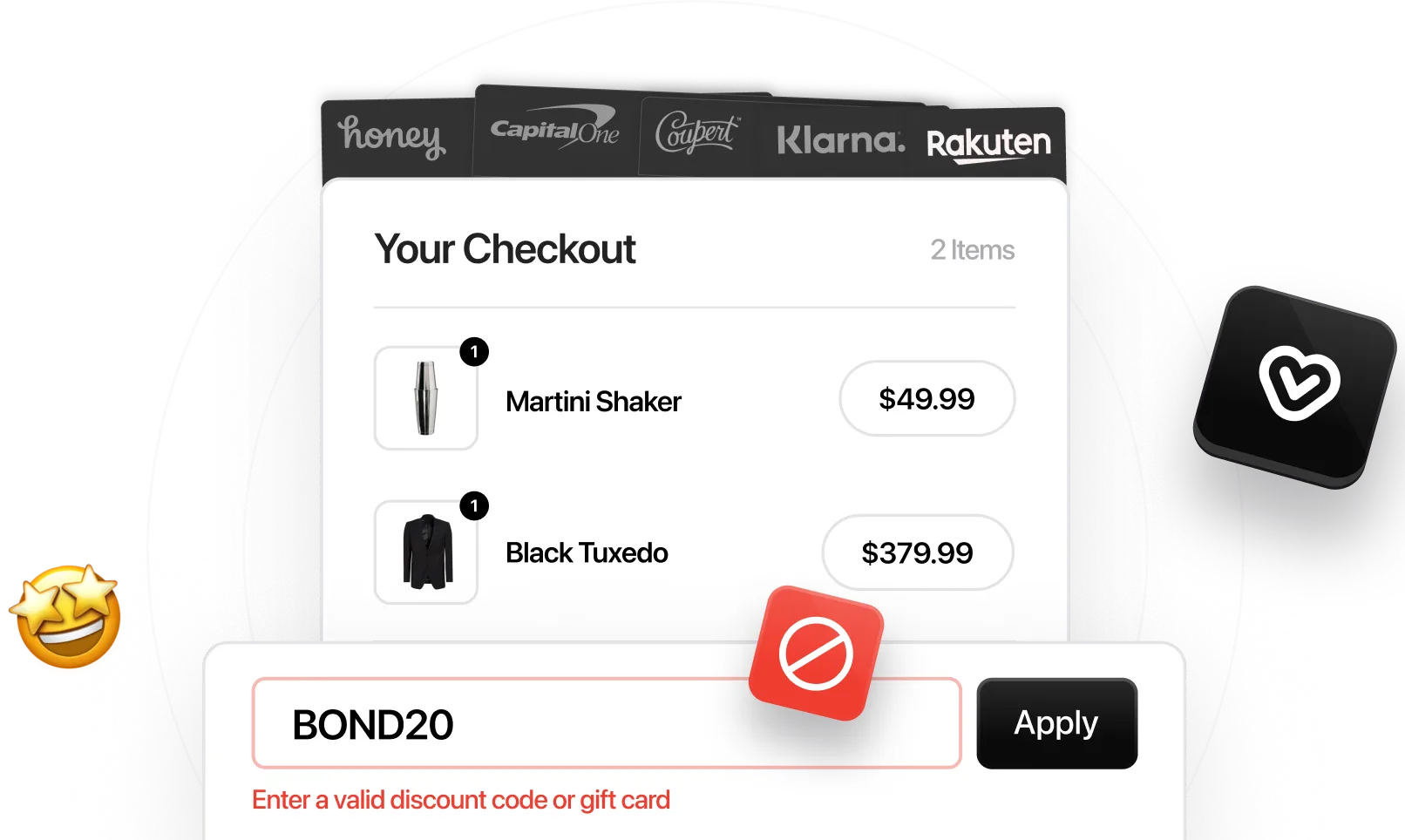
Coupon code extensions for desktop web browsers continue to be a growing and challenging obstacle for eCommerce merchants. If things weren’t already hard enough for retailers in 2022, in this past year alone Honey handed out over $2.1 billion in savings from scraped coupon codes, according to their own published reports.
In addition to the damage these extensions can cause to your revenue and marketing campaigns, their ties to third-party merchants may also pose potential security and privacy threats to customers on your site, and there is very little you as an online retailer can do to stop it.
Coupon Code Scraping
If you’re familiar with the content on our blog, you’ve probably heard us talk about all the problems coupon code extensions present to your online business. These problems begin when customers use coupon codes they’ve earned from signing up for your newsletter, following you on social media, etc., and then extensions like Honey and CapitalOne Shopping scrape those codes off your site and distribute them to unintended audiences.
This not only cuts into your calculated ROI from the discounts you have parcelled out to new or returning customers, but it also makes it difficult to track how effective your marketing strategy might have been.
Many of the codes entered by your customers may have been scraped and automatically injected by browser extensions instead of your intended targeted customer, making it difficult to tell what actually drove the sale.
These kinds of extensions also have the potential to drag customers away from your website by offering them a better deal somewhere else just as they are about to make a conversion.
Third Party Merchants
Beyond this, in recent years two of the most successful coupon extensions, Honey and CapitalOne Shopping, have been respectively acquired by major third-party merchants PayPal and CapitalOne.
This introduces a whole new set of potential issues for online retailers.
These kinds of affiliates primarily derive their revenue from the merchant services and financial transactions they handle for consumers and retail businesses. So, as a third party on your site trying to incentivize users to check out through their service (be it PayPal, Capital One, Amazon Pay, etc.), merchant owned coupon extensions like Honey can now track your transactions and identify which method of payment you used to check out.
This now arms PayPal with an amount of data that is almost an unfair strategic chess move against other vendors who could actually better service your customers.
And on top of that, these extensions are able to give a glimpse into your business that a third-party merchant does not usually have. Whether they are screen recording, collecting shopper data, or even sharing data with other merchants, PayPal is now watching and recording customers on your site without your permission.
There is no reason why PayPal should have any more ability to view your customers’ transactions than Visa or Amazon Pay, unless they would be willing to compensate you for that data.
Similar to how Google and Facebook seem to have an unbridled ability to collect data while you surf the web, third party merchants are now the new horizon of that same unregulated data harvesting.
The Problem With Coupon Extensions
We’ve used this example a couple of times now, but imagine working at the cash register at your retail establishment, and a stranger walks in offering copies of your discount coupons to customers right on the verge of making purchases—or worse, telling them they could get a better deal at a competitor just across the street (as many extensions now do).
Now imagine that stranger actually works for a credit card company and, along with disrupting your business sales, begins jotting down and recording all the purchases your customers are making without your permission.
Both situations take away a large amount of the control you have around the nature and security of the transactions happening at your own business.
Wrapping Up
As the number of coupon extensions and their reach grows, new solutions are emerging to restore the degree of control that online retailers have over them.
One example of this is Coupon Blocker™, which blocks coupon browser extensions from auto-injecting discount codes at checkout.
If you’re concerned that blocking automatic coupon extensions with products like Coupon Blocker™ may cause an adverse relationship with your shoppers, it’s important to note that over the past year, commerce has moved increasingly towards mobile devices where extensions are not able to execute.
So if anything, blocking extensions has actually disproved the idea that consumers may be unwilling to make transactions without promo codes, because the fastest growing market of eCommerce (mobile) already prevents automatic injection.
But, these automatically injected coupon codes still have the potential to wreak havoc and disrupt the security of your online business, and you should arm yourself with the right tools and information to maintain control over your users' shopping experience.